今日推荐开源项目:《成为命名大师 codelf》
今日推荐英文原文:《Would you let an AI Camera in your home?》

今日推荐开源项目:《成为命名大师 codelf》传送门:GitHub链接
推荐理由:还在为了给变量取名字而烦恼?放下你手上那本婴儿命名大全吧,它只会给你带来生命危险。这个项目能够让你简单方便的找到一个合适的变量名字——只需要 CodeLF 一下。它可以作为 VSCode,Atom 或者 Sublime Text 的插件来安装,或者也可以使用网页版。如果你想知道它究竟从哪弄来的这么多变量名,就按一下这些名字对应的 Repo 吧,它们并不是凭空出现的。
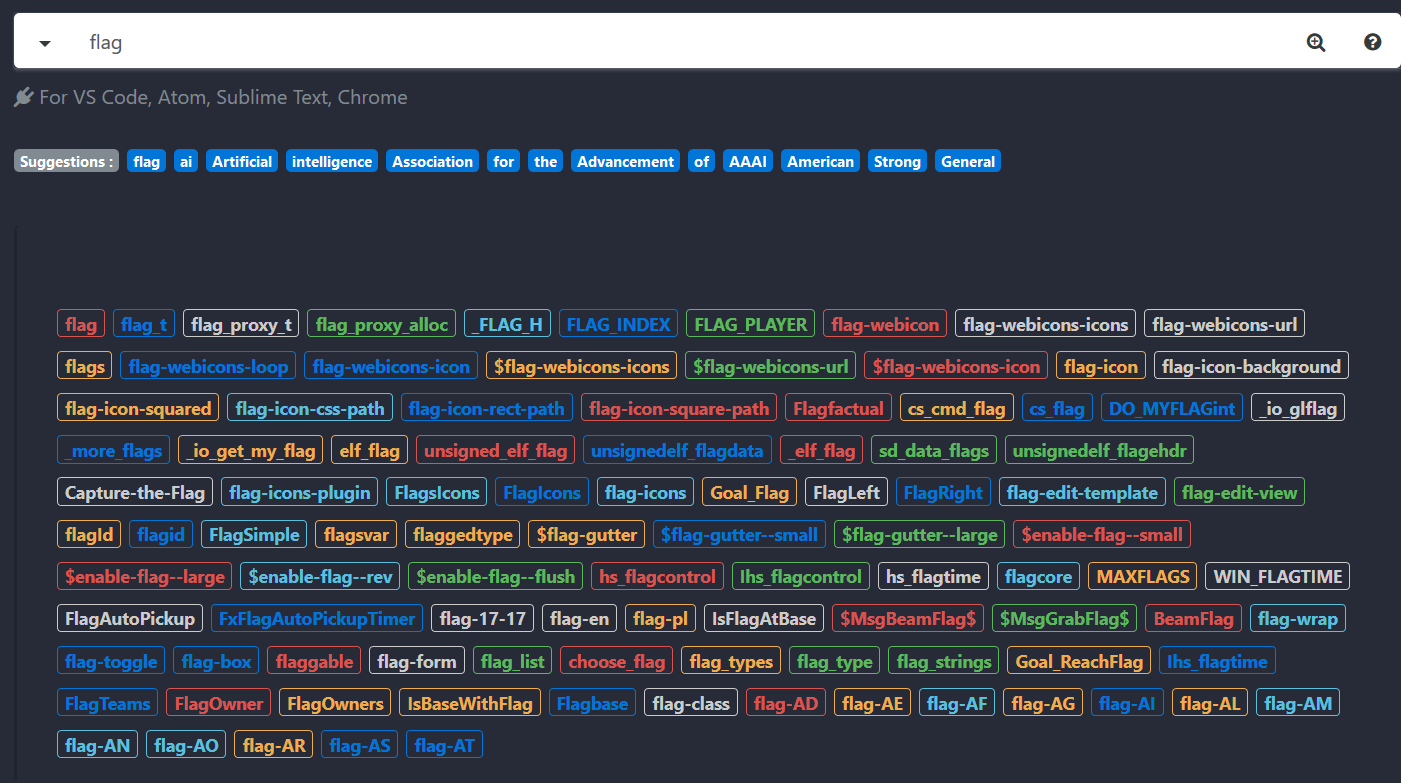
今日推荐英文原文:《Would you let an AI Camera in your home?》作者:Alexandre Gonfalonieri
原文链接:https://medium.com/swlh/would-you-let-an-ai-camera-in-your-home-1292cd558193
推荐理由:智能相机兴许会很管用,但是用它是拍不到圣诞老人的
Would you let an AI Camera in your home?

Are you thinking about buying an AI security camera for your home? It sounds like a good purchase for your home safety.
Cameras can already connect to wi-fi and have been an integral part of our smart devices for years, but they haven’t had “minds” of their own.
The world of automated surveillance is booming, with new machine learning techniques giving cameras the ability to spot troubling behavior without human supervision. Indeed, new deep learning techniques have enabled us to analyze video footage more quickly and cheaply than ever before.
This type of A.I. for security is known as “rule-based” because a human programmer must set rules for all of the things for which the user wishes to be alerted. This is the most prevalent form of A.I. for security. The hard-drive that houses the program can either be located in the cameras themselves or can be in a separate device that receives the input from the cameras.
This is one of the key driving factors behind the push to bring AI and video surveillance together. The idea is that advanced software could supplement human judgment and provide for more accurate and safe surveillance.
Cameras are really important
From saving lives to keeping us safe
Boston was full of cameras. But none of them was able to detect the threat represented by the intentionally abandoned backpacks, each containing a bomb. The video footage was predominantly analyzed by the eyes of the police department attempting to identify and locate the perpetrators. However, due to both the slow speed and low accuracy of the alternative computer-based image analysis algorithms, we might have waste time.
Automated analytics algorithms are conceptually able, for example, to sift through an abundance of security camera footage in order to pinpoint an object left at a scene and containing an explosive device or other contents of interest to investigators. And after capturing facial features and other details of the person who left the object, analytics algorithms can conceptually also index image databases from social media and private sources in order to rapidly identify the suspect.
How do artificial intelligence and embedded vision processing intersect? Computer vision is a broad, interdisciplinary field that attempts to extract useful information from visual inputs, by analyzing images and other raw sensor data. The term “embedded vision” refers to the use of computer vision in embedded systems.
Historically, image analysis techniques have typically only been implemented in complex and expensive, therefore niche, surveillance systems. However, the previously mentioned cost, performance, and power consumption advances are now paving the way for the proliferation of AI home cameras.
Why do we need AI cameras?
Let me give you an example… As more consumers move towards online shopping and have their items delivered to their doorstep, the risk of having these packages stolen has increased.

It would be great if we can stop worrying about our packages thanks to an AI camera.
Indeed, smart cameras with built-in AI capabilities offer new conveniences, like a phone notification that a child just arrived home safely, or that the dog walker really did walk the dog.
For example, many users opt to have their camera notify them as soon as it recognizes that their kids have arrived home from school. The system’s machine learning capabilities enable it to execute more complex functions, as well, such as sending an alert when an elderly live-in parent doesn’t appear in the kitchen by a certain time of day.
Facial recognition in still images and video is already seeping into the real world. Some companies have created a program where facial recognition is used instead of tickets for events. The venue knows who you are, maybe from a picture you upload or your social media profile, sees your face when you show up and knows if you’re allowed in.
All these things do improve our security, there is no question about this. However, they will also bring new risks to privacy in public and private spaces. Indeed, companies are exploring how smart cameras can be used to gather marketing data.
Limits
As great as they are, we need to be careful…
A Google patent from 2016 described how cameras in a home could use visual clues like books and musical instruments to learn about a person’s interests, and suggest content they might like. However, Google declined to comment…
Many functions envisioned for smart cameras depend on transmitting information they’ve detected, such as faces they’ve identified. We should worry that smart-home enthusiasts may give up data on themselves that they didn’t intend to share. Users of several smart speakers and other smart-home devices show they tend to blindly trust their gadgets won’t betray them, and pay little mind to privacy settings or disclosures, but for how long?
So what’s a privacy-minded, law-abiding citizen to do when surveillance becomes the norm?
Not much. Early research has identified ways to trick facial recognition software, either by specially-made glasses to fool the algorithms or face paint that throws off the AI. But these often require knowledge of how the facial recognition algorithm works.
Another issue would be that some companies are gathering data on customers through special cameras at shops and outlets so the collected information will be analyzed and their sales improved.
Indeed, an increasing number of businesses are setting up permanent cameras separately from security ones to enable recorded facial images to be analyzed with artificial intelligence.
Could such AI security cameras be trained to look for specific types of people, compounding existing biases? Is it easy to hack into the 24-hour video footage taken with these security cameras, or to hack into the AI and change its directive?
Filmed faces are regarded as a sort of citizens’ personal information. The government allows such data to be used for commercial purposes, if it is deleted after captured people’s age and other properties are analyzed, raising concerns among experts over personal privacy.
Behavior analysis is something that a lot of tech companies are researching.
Nobody wants to feel like Big Brother is constantly watching. Several companies already assure people that these systems know when to stop collecting information. For example, a camera in the home can be told to shut down when certain “intimate” situationsarise.
My opinion is that the integration of AI technology into advanced camera systems is something that’s inevitable and exciting. But if you happen to purchase one of these cameras, you need to make sure about the privacy element…
下载开源日报APP:https://opensourcedaily.org/2579/
加入我们:https://opensourcedaily.org/about/join/
关注我们:https://opensourcedaily.org/about/love/

 If you’ve checked Twitter lately, it’s hard to not have a stance on whether or not developers should be learning frameworks first or language fundamentals first (Twitter thread here) if you are a developer. With that said, and considering I’ve spent a lot of time learning fundamentals myself, I’d like to offer my opinion on the topic.
If you’ve checked Twitter lately, it’s hard to not have a stance on whether or not developers should be learning frameworks first or language fundamentals first (Twitter thread here) if you are a developer. With that said, and considering I’ve spent a lot of time learning fundamentals myself, I’d like to offer my opinion on the topic.



 One way to solve this is to incrementally ideate. Identify your core problem, what steps could be taken to solve it, and a possible solution. Next, constantly iterate the product through with your end user — maintain a constant review process to ensure the project is properly addressing the needs of your user, and remains a solution to your core problem.
One way to solve this is to incrementally ideate. Identify your core problem, what steps could be taken to solve it, and a possible solution. Next, constantly iterate the product through with your end user — maintain a constant review process to ensure the project is properly addressing the needs of your user, and remains a solution to your core problem.
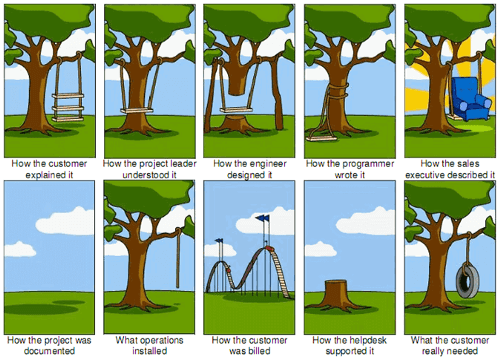 Failure to communicate at this level can cause project-shattering issues; the product could end up being severely detached from what was sold, promised, built and needed.
Failure to communicate at this level can cause project-shattering issues; the product could end up being severely detached from what was sold, promised, built and needed.
 Of course, a good plan reaches much further. A good plan or timeline can also serve as a common border for large teams, allowing them to operate quickly and efficiently in sprints. If a feature falls through or needs more time, then the plan/timeline can be adjusted quickly, and the budget adjusted accordingly.
Of course, a good plan reaches much further. A good plan or timeline can also serve as a common border for large teams, allowing them to operate quickly and efficiently in sprints. If a feature falls through or needs more time, then the plan/timeline can be adjusted quickly, and the budget adjusted accordingly.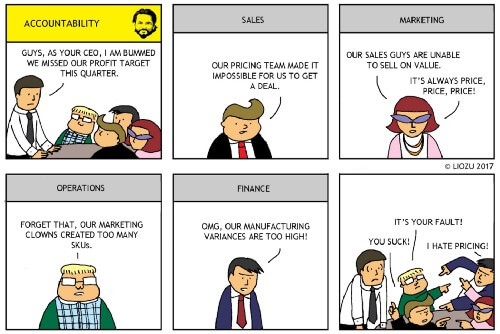 It sounds childish but a common occurrence in the software development industry is “pointing fingers.” The backend engineers will blame the frontend engineers will blame the sales team will blame the marketing team will blame the legal office will blame the management will blame… This process is not only time consuming and disastrous for morale, but it leaves the core question — “what went wrong?” — open and unanswered.
It sounds childish but a common occurrence in the software development industry is “pointing fingers.” The backend engineers will blame the frontend engineers will blame the sales team will blame the marketing team will blame the legal office will blame the management will blame… This process is not only time consuming and disastrous for morale, but it leaves the core question — “what went wrong?” — open and unanswered. What may seem like a small change at first could end up becoming a long-term development project.
What may seem like a small change at first could end up becoming a long-term development project. It’s great to follow an agile methodology and move fast, but documentation is always important. Undocumented code can lead to years of technical debt and can cause tremendous issues down the road — “what does this function do?”
It’s equally important to document the product. Every step of the process from ideation to design to execution should be well-documented to ensure that the project is easily navigable for others and stays on track. Good documentation can allow for easier project tracking — in an agile system, try a kanban board or similar to keep track of tasks!
It’s great to follow an agile methodology and move fast, but documentation is always important. Undocumented code can lead to years of technical debt and can cause tremendous issues down the road — “what does this function do?”
It’s equally important to document the product. Every step of the process from ideation to design to execution should be well-documented to ensure that the project is easily navigable for others and stays on track. Good documentation can allow for easier project tracking — in an agile system, try a kanban board or similar to keep track of tasks! The technical requirements of a project can be hard to gauge, but it is extremely vital that you do so. What may seem like a small extra addition may turn into a turducken of an issue, involving allocating additional infrastructure and redefining the entire system to introduce support.
The technical requirements of a project can be hard to gauge, but it is extremely vital that you do so. What may seem like a small extra addition may turn into a turducken of an issue, involving allocating additional infrastructure and redefining the entire system to introduce support. Often times a project is exciting and easy to jump into; however, it is vital to its success for the proper preparation to take place. Specifications need to be created, designs must be drafted, a timeline should be agreed on, and resources should be allocated.
A popular method of managing this at a technical level is Test Driven Development. Before writing a single line of code towards a project, plan out the architecture and what each piece needs to accomplish. Next, write tests to assert that each piece actually does what was intended. In this manner, you have a framework ready with set goals and can quantify progress on the development of your product.
Often times a project is exciting and easy to jump into; however, it is vital to its success for the proper preparation to take place. Specifications need to be created, designs must be drafted, a timeline should be agreed on, and resources should be allocated.
A popular method of managing this at a technical level is Test Driven Development. Before writing a single line of code towards a project, plan out the architecture and what each piece needs to accomplish. Next, write tests to assert that each piece actually does what was intended. In this manner, you have a framework ready with set goals and can quantify progress on the development of your product.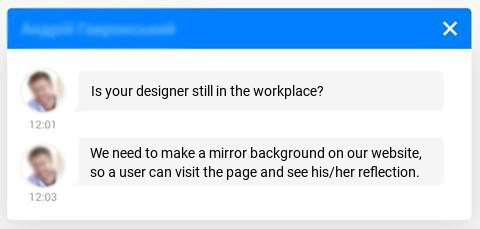 It’s important to manage expectations. Often times, the client asks for a feature that is unreasonable, impractical, or flat-out impossible. A common practice is to limit the number of changes that can be made to a spec and to have an engineer present during discussions to determine if the proposed feature is technologically feasible.
Hopefully, by avoiding these 10 pitfalls, your next software development project will be an astounding success! What issues have you run into in your software projects?
It’s important to manage expectations. Often times, the client asks for a feature that is unreasonable, impractical, or flat-out impossible. A common practice is to limit the number of changes that can be made to a spec and to have an engineer present during discussions to determine if the proposed feature is technologically feasible.
Hopefully, by avoiding these 10 pitfalls, your next software development project will be an astounding success! What issues have you run into in your software projects?