推荐理由:推特是全球著名的互联网公司,也是全球网络舆论总阵地的动向,代表了社交平台的变换趋势。
Twitter will remove inactive accounts and free up usernames in December
Twitter is sending out emails to owners of inactive accounts with a warning: sign in by December 11th, or your account will be history and its username will be up for grabs again. Any account that hasn’t signed in for more than six months will receive the email alert.“As part of our commitment to serve the public conversation, we’re working to clean up inactive accounts to present more accurate, credible information people can trust across Twitter. Part of this effort is encouraging people to actively log-in and use Twitter when they register an account, as stated in our inactive accounts policy,” a spokesperson told The Verge by email. “We have begun proactive outreach to many accounts who have not logged into Twitter in over six months to inform them that their accounts may be permanently removed due to prolonged inactivity.”
Twitter hasn’t yet said exactly when recouped usernames will be made available to existing users. The account removal process “will happen over many months — not just on a single day,” according to the spokesperson. So don’t expect some massive username rush to happen on December 12th. It might be awhile.
This doesn’t just affect people who’ve abandoned Twitter; it also stands to have an enormous impact on accounts belonging to the deceased. The Verge has asked Twitter whether those will also be pulled into the inactive pool and ultimately removed as part of this process. “We do not currently have a way to memorialize someone’s Twitter account once they have passed on, but the team is thinking about ways to do this,” the spokesperson said.
This might be your best chance to preserve tweets from deceased loved ones If you’ve set up a bot or another secondary account, you should be safe as long as it’s stayed active. The BBC’s Dave Lee reported on the username cleanup. It’s not unusual for huge online platforms to do this from time to time. Yahoo launched an “account recycling” effort in 2013, though some people who grabbed inactive usernames wound up receiving email intended for the old account holder.
Keep in mind that these accounts don’t have to actually tweet anything to stick around. They just have to log in and follow Twitter’s instructions. So even if the username you want seems long dormant based on activity, whoever owns it can still hold on to the username pretty easily.
Also, usernames with under five characters can no longer be registered on Twitter, so that’s another thing to consider when dreaming about switching to that username you’ve always wanted. The username some other fool is failing to put to good use.
The email being sent out has a subject line of “Don’t lose access to @(username).” Here’s what it says:
Hello,
To continue using Twitter, you’ll need to agree to the current Terms, Privacy Policy, and Cookie Use. This not only lets you make the best decisions about the information that you share with us, it also allows you to keep using your Twitter account. But first, you need to log in and follow the on-screen prompts before Dec. 11, 2019, otherwise your account will be removed from Twitter.
So which username will you be going for? Actually, probably best to keep that to yourself until it’s locked in.
下载开源日报APP:https://opensourcedaily.org/2579/
加入我们:https://opensourcedaily.org/about/join/
关注我们:https://opensourcedaily.org/about/love/
开源日报 每天推荐一个 GitHub 优质开源项目和一篇精选英文科技或编程文章原文,坚持阅读《开源日报》,保持每日学习的好习惯。 今日推荐开源项目:《ImportExcel》
今日推荐英文原文:《Twitter will remove inactive accounts and free up usernames in December》

今日推荐开源项目:《ImportExcel》传送门:GitHub链接
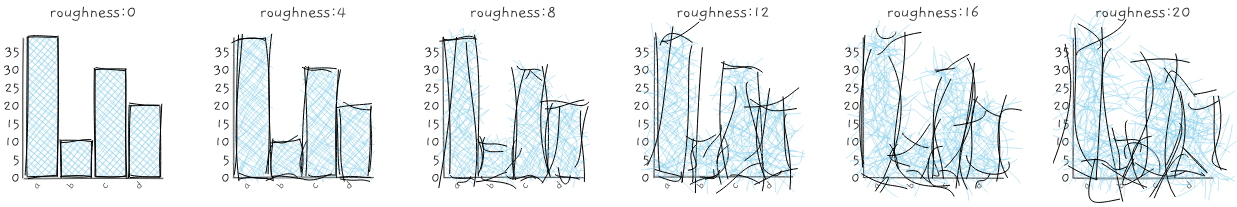
推荐理由:Excel 作为 Office三件套中的一员,强大的功能使其拥有很高的出场率。通过此 PowerShell 模块,您可以读写 Excel 文件,而无需在系统上安装 Microsoft Excel 。无需麻烦的 Excel COM 对象。创建表格,数据透视表,图表等等变得更加容易。
今日推荐英文原文:《Twitter will remove inactive accounts and free up usernames in December》
原文链接:https://www.theverge.com/2019/11/26/20984328/twitter-removing-inactive-accounts-usernames-available-date
推荐理由:推特是全球著名的互联网公司,也是全球网络舆论总阵地的动向,代表了社交平台的变换趋势。
Twitter will remove inactive accounts and free up usernames in December
Twitter is sending out emails to owners of inactive accounts with a warning: sign in by December 11th, or your account will be history and its username will be up for grabs again. Any account that hasn’t signed in for more than six months will receive the email alert.“As part of our commitment to serve the public conversation, we’re working to clean up inactive accounts to present more accurate, credible information people can trust across Twitter. Part of this effort is encouraging people to actively log-in and use Twitter when they register an account, as stated in our inactive accounts policy,” a spokesperson told The Verge by email. “We have begun proactive outreach to many accounts who have not logged into Twitter in over six months to inform them that their accounts may be permanently removed due to prolonged inactivity.”
Twitter hasn’t yet said exactly when recouped usernames will be made available to existing users. The account removal process “will happen over many months — not just on a single day,” according to the spokesperson. So don’t expect some massive username rush to happen on December 12th. It might be awhile.
This doesn’t just affect people who’ve abandoned Twitter; it also stands to have an enormous impact on accounts belonging to the deceased. The Verge has asked Twitter whether those will also be pulled into the inactive pool and ultimately removed as part of this process. “We do not currently have a way to memorialize someone’s Twitter account once they have passed on, but the team is thinking about ways to do this,” the spokesperson said.
This might be your best chance to preserve tweets from deceased loved ones If you’ve set up a bot or another secondary account, you should be safe as long as it’s stayed active. The BBC’s Dave Lee reported on the username cleanup. It’s not unusual for huge online platforms to do this from time to time. Yahoo launched an “account recycling” effort in 2013, though some people who grabbed inactive usernames wound up receiving email intended for the old account holder.
Keep in mind that these accounts don’t have to actually tweet anything to stick around. They just have to log in and follow Twitter’s instructions. So even if the username you want seems long dormant based on activity, whoever owns it can still hold on to the username pretty easily.
Also, usernames with under five characters can no longer be registered on Twitter, so that’s another thing to consider when dreaming about switching to that username you’ve always wanted. The username some other fool is failing to put to good use.
The email being sent out has a subject line of “Don’t lose access to @(username).” Here’s what it says:
Hello,
To continue using Twitter, you’ll need to agree to the current Terms, Privacy Policy, and Cookie Use. This not only lets you make the best decisions about the information that you share with us, it also allows you to keep using your Twitter account. But first, you need to log in and follow the on-screen prompts before Dec. 11, 2019, otherwise your account will be removed from Twitter.
So which username will you be going for? Actually, probably best to keep that to yourself until it’s locked in.
下载开源日报APP:https://opensourcedaily.org/2579/
加入我们:https://opensourcedaily.org/about/join/
关注我们:https://opensourcedaily.org/about/love/